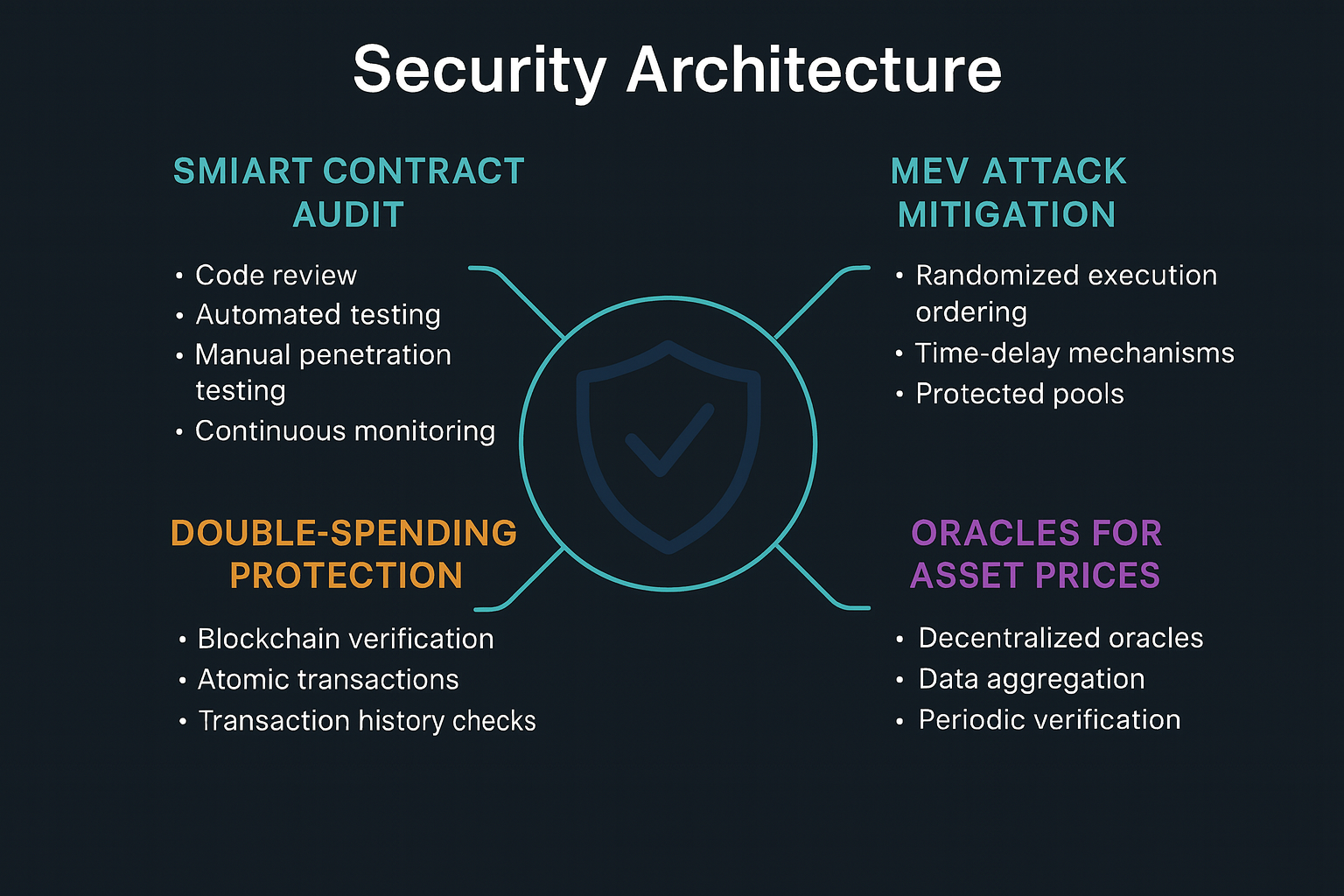
Security Architecture
The security architecture of our platform is designed to provide a robust and resilient ecosystem for traders while ensuring the integrity of all in-game and blockchain transactions. Security is a cornerstone of trust in any decentralized financial game, and we implement multiple layers of protection to prevent exploits, hacks, and unfair advantages.
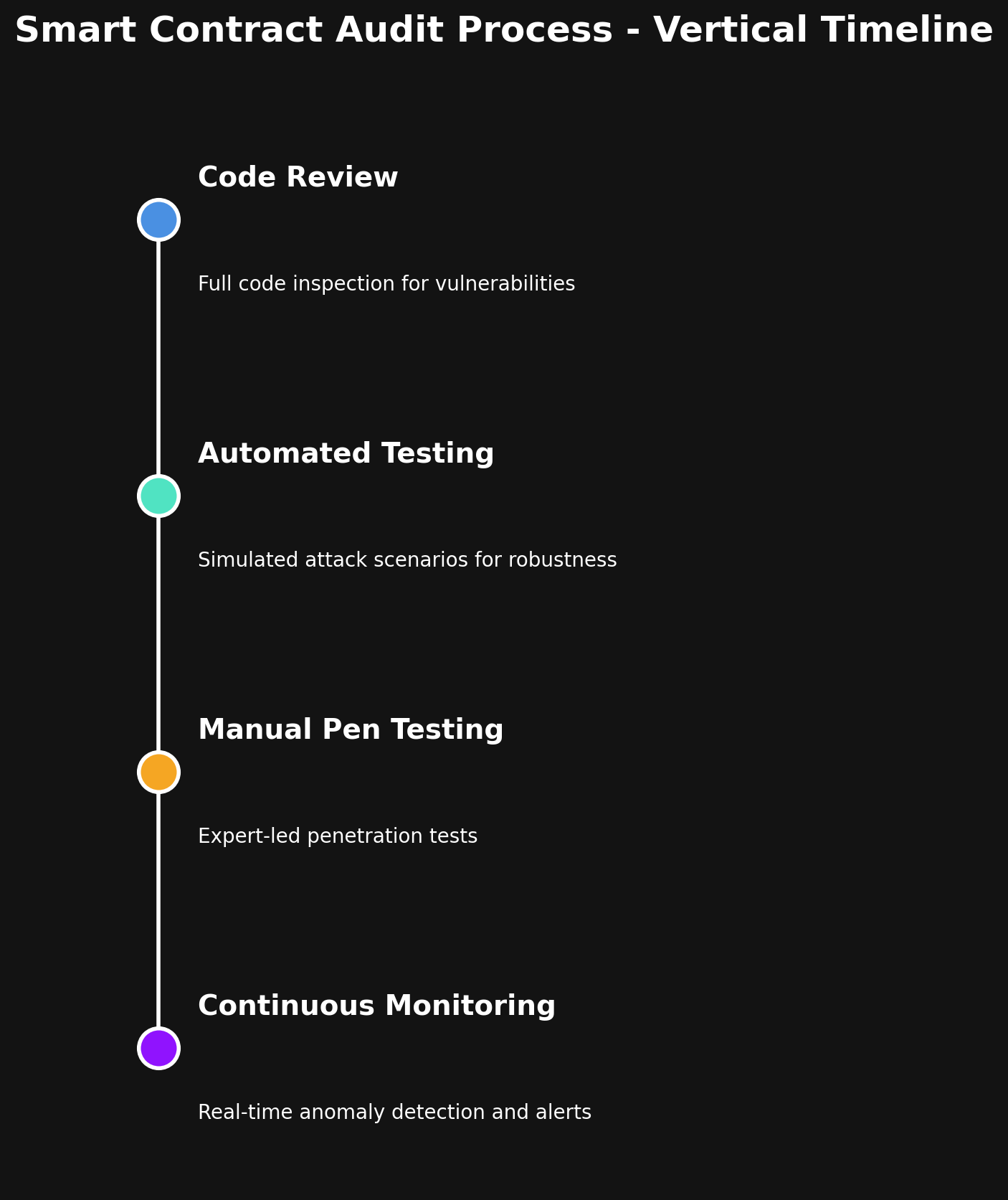
1. Smart Contract Audit
All smart contracts within the Trading Battle ecosystem are subject to rigorous audits by top-tier blockchain security firms before deployment. The audit process includes:
- Code review: Every function, variable, and access control mechanism is reviewed to identify vulnerabilities such as reentrancy, integer overflows, and improper access control.
- Automated testing: Specialized tools simulate various attack scenarios, ensuring contracts behave as expected under edge conditions.
- Manual penetration testing: Security experts attempt to exploit contracts in controlled environments to identify potential risks.
- Continuous monitoring: Post-deployment, contracts are monitored for abnormal interactions or suspicious activity.
The audit ensures that the TBT token, in-game staking mechanisms, and reward distribution protocols are secure and resistant to manipulation.
2. MEV (Maximal Extractable Value) Attack Mitigation
MEV attacks—where miners or validators manipulate transaction ordering for profit—pose a threat to fairness in trading platforms. To mitigate MEV:
- Randomized execution ordering: Transaction execution in duels and tournaments is randomized to prevent predictable exploitation.
- Time-delay mechanisms: Strategic delays in transaction confirmation reduce the feasibility of front-running attacks.
- Protected pools: Critical contract interactions, such as reward distribution, occur within MEV-protected pools.
These measures ensure that players’ predictions, staking, and winnings cannot be unfairly exploited by network actors.
3. Double-Spending Protection
In any digital asset system, double-spending—using the same tokens more than once—is a critical threat. Our platform prevents double-spending through:
- Blockchain verification: All TBT transactions are validated on the Binance Smart Chain (BSC), leveraging its decentralized consensus.
- Atomic transactions: Token transfers for duels, rewards, and marketplace purchases are executed atomically, ensuring either full completion or full rollback.
- Transaction history checks: Each wallet and transaction undergoes real-time validation to detect and block duplicate usage attempts.
This ensures that all TBT token operations are reliable and tamper-proof.
4. Oracles for Asset Prices
Accurate and timely price data is crucial for trading simulations. To maintain fairness:
- Decentralized oracles: Our platform integrates multiple decentralized oracle providers to fetch real-time market prices from reliable exchanges.
- Data aggregation: Prices from multiple sources are aggregated to avoid reliance on a single feed, reducing the risk of manipulation.
- Periodic verification: Historical price checks and anomaly detection algorithms ensure the data’s integrity and prevent outlier manipulation.
Oracles are critical for determining winners in price-based duels, ensuring that gameplay remains transparent and fair.
The layered security architecture of Trading Battle combines blockchain best practices, advanced attack mitigation techniques, and real-time data verification to create a secure and trustworthy gaming environment. Players can confidently engage in duels, tournaments, and marketplace activities knowing that the system safeguards both their assets and the integrity of the game.