Consensus & Network Details
1. Consensus Algorithm
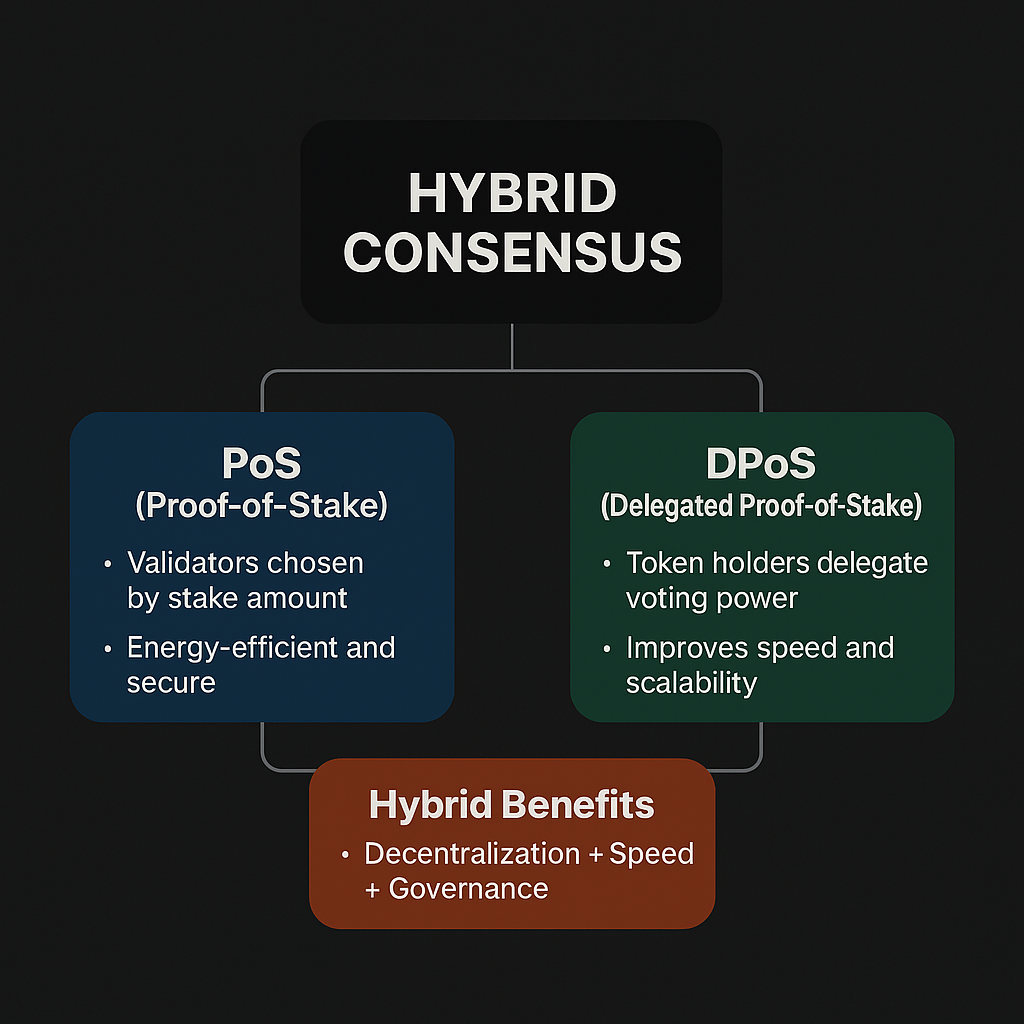
Our platform employs a hybrid Proof-of-Stake (PoS) / Delegated Proof-of-Stake (DPoS) consensus mechanism to achieve a balance between decentralization, speed, and security:
- Proof-of-Stake (PoS): Validators are selected based on the amount of TBT tokens they stake. The higher the stake, the higher the chance of being chosen to propose and validate blocks. This method reduces energy consumption compared to Proof-of-Work (PoW) while still ensuring security and fairness.
- Delegated Proof-of-Stake (DPoS): Token holders can delegate their TBT to trusted validators, creating a network of active representatives. This enhances scalability and throughput, as fewer nodes are involved in block validation, while stakeholders maintain governance rights by voting on delegates.
- Hybrid Benefits: Combining PoS and DPoS allows the system to maintain decentralization, fast block times, and efficient consensus while enabling governance participation and community oversight.
2. Validator Requirements
To maintain the integrity and performance of the network, validators must meet certain technical and financial criteria:
- Staking Requirement: A minimum TBT stake is required to participate in validation. This ensures validators have skin in the game.
- Hardware Specifications: Validators must run nodes with high uptime, secure servers, and reliable network connections to reduce latency.Recommended specs include:
- CPU: 8 cores or more
- RAM: 32 GB+
- Storage: SSD 1TB+ with redundancy
- Security Compliance: Validators must implement strict security measures, including firewalls, encrypted communication channels, and multi-factor authentication.
- Reputation System: Validators’ performance is tracked (uptime, correctness, and response time), affecting their eligibility and reward share.
3. Performance Metrics: TPS, Latency, and Scalability
- Transactions Per Second (TPS): The network is designed to handle 5,000–10,000 TPS, accommodating real-time trading in the game and large-scale user activity.
- Latency: Optimized for sub-second block finality, ensuring player actions, staking, and rewards are recorded almost instantly.
- Scalability:
- Horizontal Scaling: Adding new validators and shard chains increases capacity without affecting performance.
- Off-chain Solutions: Integration with Layer 2 solutions for microtransactions, reducing main-chain load and gas fees.
- Dynamic Load Balancing: Network monitors transaction load and dynamically routes traffic to prevent bottlenecks.
4. Network Security & Cryptography
Security is critical, given the economic value of TBT tokens and the competitive nature of the platform. The network employs state-of-the-art cryptography:
- AES-256 Encryption: All player data, transaction details, and communication between nodes are encrypted using AES-256, providing military-grade confidentiality.
- RSA-2048 Encryption: Used for key exchange, digital signatures, and secure communication between validators and clients. RSA-2048 ensures that even if the network is targeted, private keys and transactions remain protected.
- Multi-layered Security:
- Validator Authentication: Node identity is verified cryptographically.
- Anti-DDoS Measures: Network architecture prevents Distributed Denial-of-Service attacks.
- Continuous Auditing: Smart contracts and protocol upgrades undergo automated and manual security audits.
- Recovery Protocols: Mechanisms for fork resolution and emergency validator replacement prevent systemic failures.
- Additional Protections: The system integrates rate-limiting, anomaly detection, and consensus fault tolerance, ensuring the network can survive attacks while maintaining high availability and integrity.